The cloud provides new ways to communicate but also new channels and techniques through which hackers can penetrate your organization. With the new conveniences comes new risks.
As the most used cloud email and collaboration platform in the world, Microsoft is also a primary target for hackers. A drawback to its widespread accessibility is that hackers routinely test their attacks on Microsoft security to ensure they can bypass its checks.
Based on analysis of 55.5 million emails, 25% of phishing attacks sent to Office 365 accounts will make it to the inbox.
Originally built to secure on-prem email, providers have attempted to adapt secure email gateways to the cloud. However, they suffer from many shortcomings due to their non-native design. The largest deficiency is their impediment to existing security. Their required changes to MX records impairs or completely erases the embedded filters, meaning that instead of adding security scans they completely replace the default, obfuscating the value from those inherent layers.
Avanan adds a layer of security after the default security or any gateway that may be in place to catch the attacks that they miss.
Patented architecture - learn more
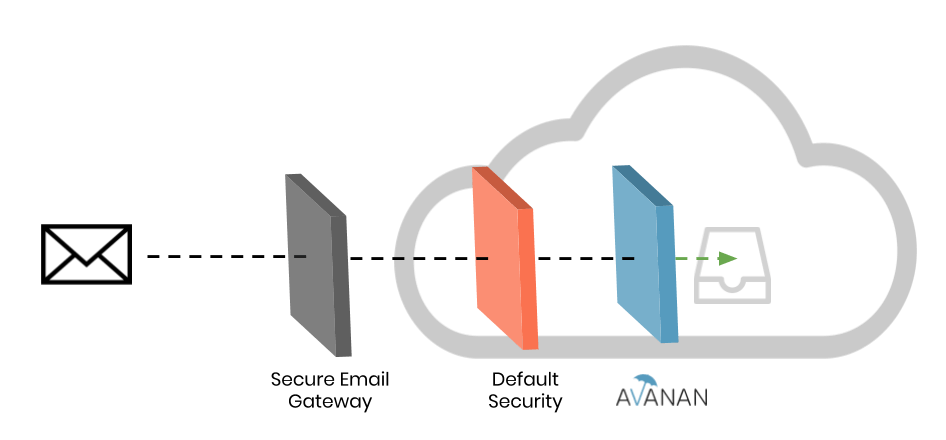

Avanan is the only security solution that connects to the cloud using native APIs while maintaining the ability to block threats before they make it to the inbox.
Learn why Avanan catches what others miss.
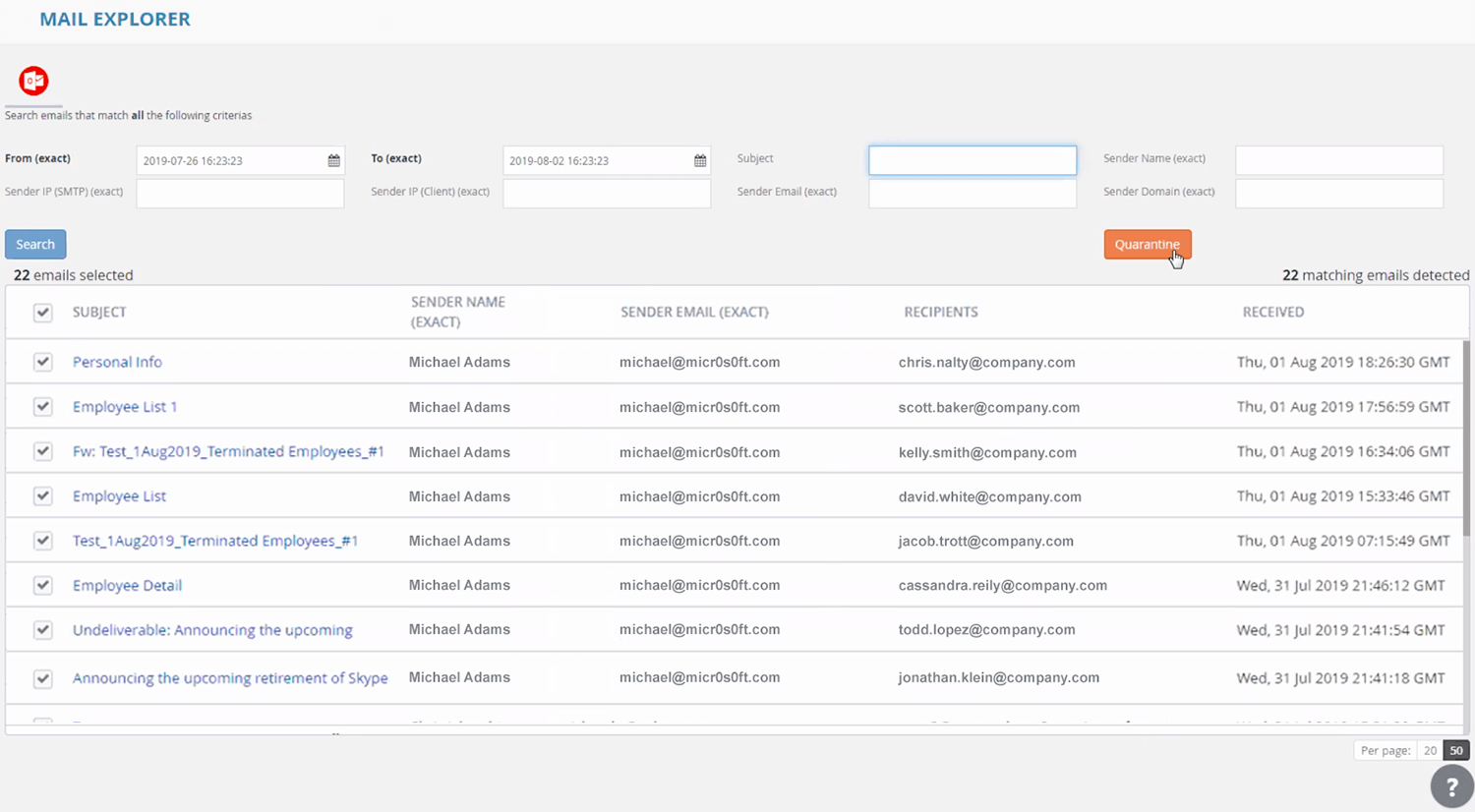
Avanan enables you to find and remove entire phishing campaigns from users inboxes based on sender, subject line, or dozens of other criteria.
Watch the 2-minute video on post-attack protection.
Avanan extends security beyond just cloud email to protect the entire suite from OneDrive to Slack to Google Drive to Teams and more.

Deploying like an app, Avanan takes only a few minutes to set up and begin securing your organization. There is no need for complicated configurations, just accept the permissions and you’re ready to go.
Watch
how Avanan deploys in one click
(1-minute video)

Approve the Avanan app in one click and start blocking phishing, malware, and other advanced threats that have evaded existing security.
